
Information Security Policy
Information Security Governance and Strategies
Xintec has established Proprietary Information
Protection Committee (PIP Committee) since January, 2008 to protect
company and customer’s confidential information. PIP Committee is
responsible for managing and supervising the control of confidential
information, and also they enact “Confidential Information Protection
Policy” and “Confidential Information Protection Management Regulation”
which clearly list management policies, procedures, and specifications
of confidential information protection. Xintec’s Information security
objective is to build a complete information security system and
comprehensive security defensive ability to ensure information security.
Identify risks, prevent and improve weakness through various security
technologies. Make employees have correct concept and awareness on
information protection, and reduce the risks from information leakage
and cyber-attacks. Maintain company’s competitive advantages.
5 main goals; fulfill PDCA Cycle:
1. Build and fulfill confidential information and
information security management system.
2. Comply with requests from the laws and contractual
obligations related to information security.
3. Indeed give education and propaganda about
confidential information protection and information security to
employees and related groups.
4. Assess and identify risks. Set a goal for improving
and control measures.
5.Improve information security management system
through internal audit.
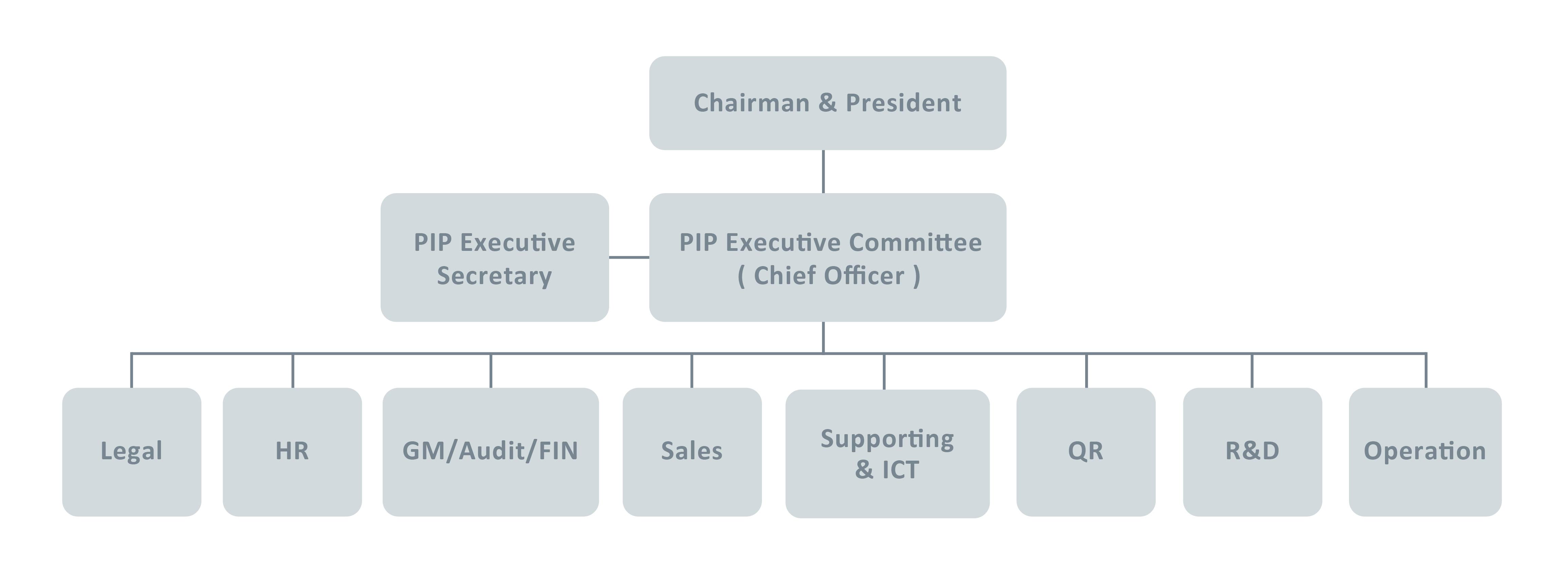
Information Security Organizations
PIP Committee’s duty is to manage, plan, supervise, and
promote departments for information security. PIP Committee and IT
department would together build a complete system and comprehensive
defensive ability. Meetings would be held seasonally by the Committee
members to check information security policy and its result. Annually,
PIP Committee would make report to the board, letting the board
understand situations of implementing information security.
1.PIP Committee: It is composed of representatives
assigned by each department head. Duty: Discuss, establish, audit, and
promote confidential information security controls.
2.PIP Executive Department: Plan, supervise, and promote
confidential information security controls
3.IT: Build and manage information security system.
Assist in evaluating, setting up and managing software and hardware
based on PIP Committee’s decision and requirement. Conduct abnormal data
of communication and information storage analysis. If there is any
abnormality, notify PIP Committee.
Risks Management and Resources
1.Strengthen information security defense, evaluate and
improve the weaknesses of external services through the third-party
security risk management platform.
2.Make emergency response plan and drill. Clearly enact
Recovery Time Objective (RTO) and Recovery Point Objective (RPO) of the
main business. Settle proper backup system and backup plan.
3.Regularly hold hazard identification, risk assessment,
and improvement operation.
4.Set up a Security Operation Center (SOC) to control
real-time information security status, focus on relative events, manage
the rising alarm, and become the command center when any issue happens.
5.Social Engineering – Phishing email, drill and cases
propaganda.
6.Regularly hold propaganda and conduct audit to check
the implementation of confidential information protection
7.Indeed conduct training for employees to enhance
employees’ information security awareness and capacity.
2022 Training and Audit
1.Total 11 PIP management meetings and 2 PIP Committee
meetings.
2.All employees in company completed 2 PIP trainings and
audits in 2022.
3.IT personnel, total 21 trainings, 44 participants, and
55 hours were done in 2022
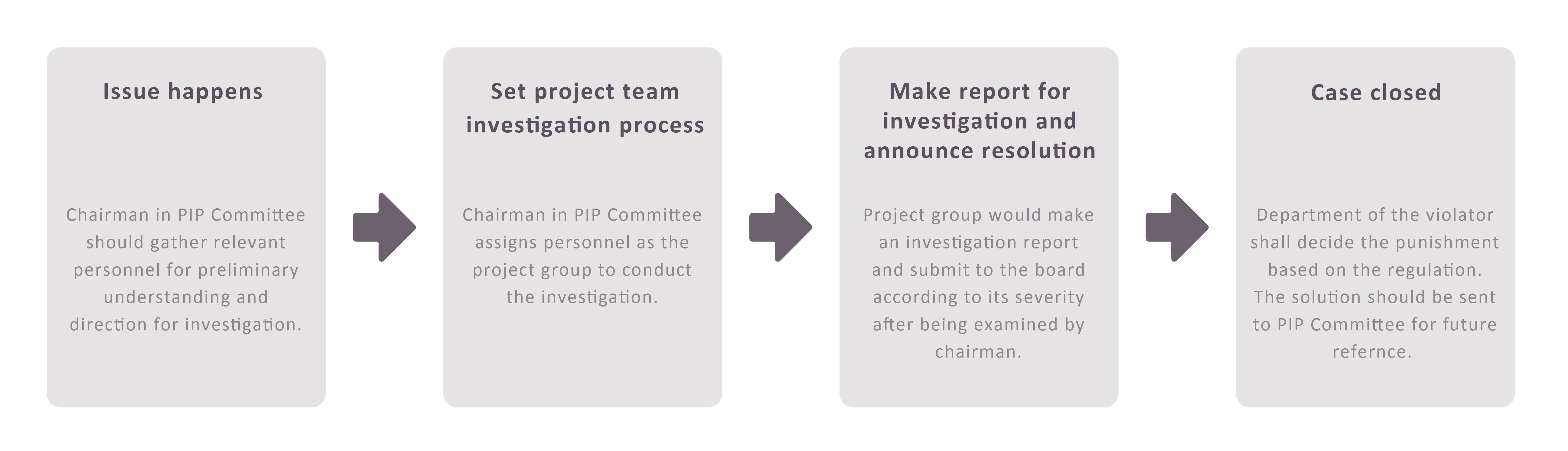
Information Security Issues
Flow for investigation:
Company didn’t get loss from serious information
security issue in 2022.
.png)
.png)

